Modern computer processors lack the security to prevent software and hardware attacks, including:
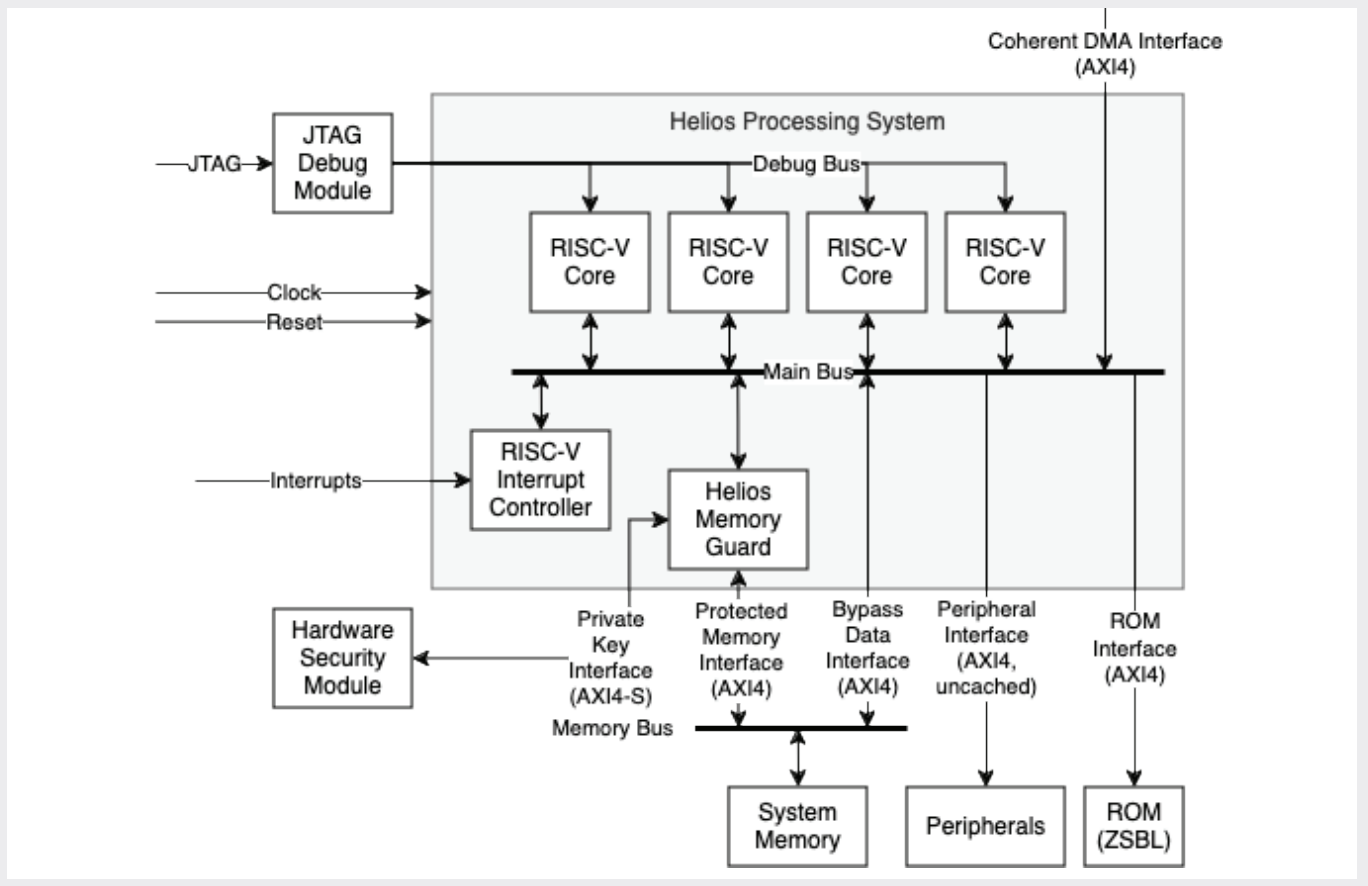
A Helios Processing System (HPS) integrates Helios Memory Guard (HMG) with a processor to provide a fully integrated and validated secure processor IP package. For load-time security, instructions and data are decrypted and authenticated against the software developer’s and/or original equipment manufacturer’s keys. For runtime security, HPS decrypts and authenticates every instruction and data cache line—in hardware—using ephemeral keys that roll on every write. Additionally, HPS enforces cryptographic isolation and authentication of instructions and data, ensuring instructions cannot be authored by an adversary at runtime.
HPSs have been verified for use with Xilinx ® 7-Series, Ultrascale, Ultrascale+, and Versal. An HPS can be ported for use with other FPGA vendor devices.
Yes, the HMG has been taped out in 28nm as part of a Helios Processing System that uses RISC-V core. Additional ASIC projects are underway.
Yes, the Helios Memory Guard can be integrated with ARM and other CPU Designs.
Idaho Scientific provides the software “Packager” utility, allowing the OEM or endcustomer to generate and manage their own cryptographic keys.
256-bit AES-GCM for both inline memory and data-at-rest load time encryption and verification. MLDSA-87 used for key management, with RSA-3072 provided for legacy support.
All HPS offerings can be configured with all relevant software security extensions ratified in RISC-V, including Shadow Stacks (Zicfiss), Landing Pads (Zicflap), RISC-V Cryptography Extensions (Volume I and II), Physical Memory Protections (PMP), and Virtual Memory Management (Sv32, Sv39, and Sv48).
System designers can anticipate <6% impact to software execution performance when running on a Helios-enabled CPU. A detailed performance white paper is available for review.
The NOEL-V HPS is capable of 1.33 instructions per cycle, 5+ SpecIn2K6/GHz and 7+ CoreMarks/MHz FPGA users can plan on 200 MHz core clock and ASIC users can exceed 1.5 GHz. Performance information for the RPX-105 HPS is available upon request.
